System Specific Security Policy
System specific security policy. An Issue-specific policy is concerned with a certain functional aspect that may require more attention. Click to see full answer. Systems- Specific Policy SysSP Appear with the managerial guidance expected in a policy Include detailed technical specifications not usually found in other types of policy documents Managerial Guidance SysSPs Guide the implementation and configuration of a specific technology Technical Specifications SysSPs General methods for implementing technical controls Access control lists Set.
Enterprise information security policy EISP Issue-specific security policy ISSP Password policy Remote access policy System-specific policies SysSPs Policy for the payroll system. A System-specific policy is concerned with a specific or individual computer system. To implement widespread changes to a systems security policy as specified by SCA right-click Security Configuration and Analysis and select Configure Computer Now.
Issue-specific policies may cover electronic mail use of internet Home use of company-owned computer equipment use of personal equipment on company networks use of telecommunications. Issue-Specific Security Policy is one among three other Information security Policy. Security policy is a definition of what it means to be secure for a system organization or other entity.
Gaming station and use of TV network should be authorized and monitored. Identify the importance and functions of Governance Risk Management and Compliance in Cybersecurity program management. Those are some explanations about security policy examples their uses and functions as well as several types.
The changes will be updated on the local computer. A how to select configure or operate a firewall b access. All access to electronic messages must be limited to properly authorized personnel.
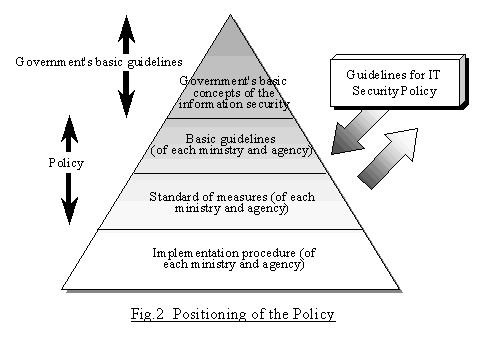
It is limited in its application to systems that are affectedby changes in the entire system with regard to its functionality andvulnerabilities. It is the strategic plan for implementing security in the organization. Thereof what is a system security policy.
3 System-Specific Security Policy System-specific security policies SysSPs frequently do not look like other types of policy They may function as standards or procedures to be used when configuring or maintaining systems Eg. A System-Specific Security Policy is different from a typical Enterprise Information Security Policy or Issue-Specific Security Policy in that it governs how one particular system is set up and maintained.
To implement widespread changes to a systems security policy as specified by SCA right-click Security Configuration and Analysis and select Configure Computer Now.
General or security program policies. General or security program policies. Security policy is a definition of what it means to be secure for a system organization or other entity. Describe the structure and content of Cybersecurity-related strategy plans and planning Identify the key components and. The usage of the E-Mail system is subject to the following. Describe best practices in risk management including the domains of risk assessment and risk treatment. A how to select configure or operate a firewall b access. A System-specific policy is concerned with a specific or individual computer system. Issue-specific security policies Systems-specific security policies.
Thereof what is a system security policy. Click to see full answer. E-Mail must be used in compliance with the Corporate Security Policy and associated Supplementary Information Security Policies. It is meant to present the approved software hardware and hardening methods for that specific system. Those are some explanations about security policy examples their uses and functions as well as several types. 3 System-Specific Security Policy System-specific security policies SysSPs frequently do not look like other types of policy They may function as standards or procedures to be used when configuring or maintaining systems Eg. A how to select configure or operate a firewall b access.













































Post a Comment for "System Specific Security Policy"